Most of the conversations with the customers, three subjects are discussed prominently, 1️⃣ Digital transformation, 2️⃣ Vendor agnostic cloud, and 3️⃣ Cyber-security. Part of digital transformation is providing services faster at lower cost and these services can be accessed from any time, anywhere. This is the reason for many organizations “Cloud First” is becoming a new norm. Cloud hosting provides a multitude of benefits, but it’s also important to remain vigilant and realistic about what data is stored, where, and how it is protected.
While making the decision to go for multiple clouds, organizations are considering few decision-making factors. These factors are including but not limited to:
1️⃣ Meet technology requirements of specific workload or application
2️⃣ Geographic benefits from the point of latency
3️⃣ Availability of cloud hosting facilities in the region to comply data privacy requirements
4️⃣ Mitigating vendor locking risks
5️⃣ Greater flexibility and agility to adapt to high demand from business to getting products services faster to the market and still be competitive
6️⃣ The Industry specific cloud hosting e.g. Public sector, government or healthcare cloud
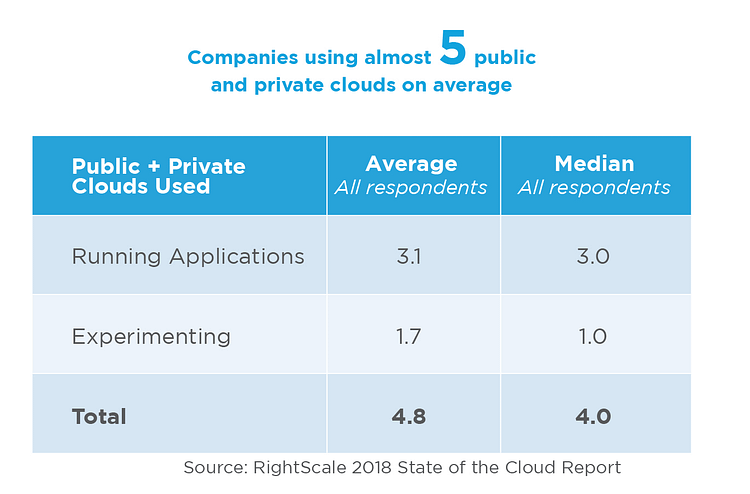
The trend “why” and “how” the organizations are adopting cloud is changed. Organizations have become accustomed to a multi-cloud or hybrid cloud environment. As per the RightScale 2018 State of the Cloud Report™, 81% of organizations are now utilizing multi-cloud environment. And on an average, these organizations are using 5 different public or private clouds.
Cyber Security Challenges in the Multi-Cloud Environment
Before discussing security concerns of Multi-cloud, Hybrid- Cloud environment, let us understand when the term Multi-Cloud is used and When hybrid cloud.
As per Radhesh Balakrishnan, general manager, OpenStack, Red Hat
“Multi-cloud is one wherein you mix and match cloud services from different providers, often to meet specific workload needs, but no connection or orchestration between them”.
For example, the Multi-Cloud environment can be the combination of IaaS (Infrastructure as a Service) form one CSP (Cloud Service Provider) and SaaS from another vendor (Software as a Service) environment.
Hybrid cloud environment includes private and public cloud services. Most of the time journey to migrate workloads to cloud starts here. In this case, organizations can maintain high risk or business-critical applications hosted in the data center and migrate low-risk workloads to the cloud to get acquainted with the cloud.

Though these environments sound different the security concerns of both these environments are similar, not having a single layer of orchestrating, and all the security and regulatory compliance requirements across all the cloud providers has resulted into many other concerns.
Multi-cloud environments add to the existing cloud security challenges. Following are the challenges security professionals needs to take care of while designing the security for multi-cloud and or Hybrid cloud environment:
- Lack of security posture visibility– Since your workload(s)/applications are distributed across the clouds, there will not be visible to the security posture as an organization. Security will be depending on the CSP and the tools and technologies that can be used and integrated with CSP tools and technologies.
- Compliance with the organization policies & regulatory requirements — It becomes increasingly difficult as the number of players in the security area is increasing. Translating your organization’s security policies into the multiple and different vendor technologies areas can be a daunting task for security professionals. Assessing the compliance as per regulatory requirements will be another area where assessments and visibility to the reports dependent on the CSP.
- Shadow IT — One of the Cloud services advantages is fast on-boarding virtual machines, storage, and applications. This advantage is also a reason for the fast growth of shadow IT. To become more productive, business units and individuals can make their own purchase decisions without the involvement of IT, leading to the presence of data assets outside IT’s control. This creates the problem of protecting the data assets, deploying the policies and processes to maintain the security posture of the organizations.
- Decentralized information and Distributed Security Controls — Each CSP has their own security tools/technologies available to be utilized efficiently and effectively for their platform. This becomes a challenge to Security teams as integrating all these tools and getting a centralized view of vulnerabilities, policy enforcement, and security incidents become challenging. This also impacts the effectiveness and efficiency of the security professionals as they cannot perform multi-tasking and need to acquire the skill to monitor and manage different toolsets for the same task. Security technologies deployed across the multiple clouds/environments need to be able to share the threat intelligence to stop the attack at early stages of kill chain. Since the security logs will be generated at multiple cloud environments in different formats. Getting these logs at a centralized location for defining the correlation, performing the analysis is not impossible but difficult if the hosting facilities of CSPs are geographically separate.
- Managing Identities across the clouds — This challenge involves timely and secure management of user onboarding and offboarding i.e. provisioning and deprovision of the users. The challenge may be existing in-house IDAM solution cannot be extended OR needs a major upgrade to provide federated IAM. Security professionals always having a challenge of providing users with the flexibility to seamlessly move around the environment while still maintaining appropriate security levels — or more specifically, ensuring consistent control and security policy between multiple cloud services and on-premise applications.
- Added efforts to compliance audits and risk assessments — From the business point of view “Security” is about managing the risks. In case of the multi-cloud environment, integration of tools like Identity Access Management, encryption may introduce additional risks. Managing and maintain the asset inventory and defining the business priorities becomes difficult and this can hamper the risk management. The GRC team need to spend more time and efforts on getting the unified view of risks across the distributed environment.
How to Manage These Challenges?
While designing cloud security architecture one should consider an architecture that protects users, safeguards data, and better addresses regulatory compliance requirements. And also consider that all the components that consist of the Multi-cloud environment should have consistent security. The other cloud security considerations like encryption of data, secure communication links, managing the encryption keys and certificates are the must-have controls.
1️⃣ Legal Involvement — Starting any cloud migration project, it is important to involve a legal team to validate the CSP contract(s). In case of the multi-cloud environment, the output of comparison between different CSP contracts can be used for making a decision which workload to be hosted in which environment. These contracts also provide the important inputs how the Incident will be managed and data breach in multi-tenancy environment will be handled. What, when, how the required data for incident management and forensic investigation will be shared.
2️⃣ Visibility — One of the most important aspects is the ability to gain even visibility and insight to your own resources and resources of cloud service providers. The security professionals need a single dashboard that can give them insight into what resources are being used and how services are related to each other.
To avoid the shadow IT problem, the business rules need to be created, these rules can define which users can provision the resources and what types of resources can be provisioned. Role Based Access Control (RBAC) becomes all the more important to provide the right level of access to right users to perform their duties and at the same time maintain need to know access provisioning principle.
Getting visibility to the attacks those are not directed to your environment and how those will be handled is another important point that needs to be considered. e.g. DDoS attack or the virus infection to the shared infrastructure
3️⃣ Data Availability — Nowadays most of the cloud service providers provide the portability so you can migrate workloads to another cloud service provider. However, it is very easy to move the virtual machines but when it comes to moving the data sets it is not that easy and hence you need to make sure that data back-up is automated and restoration of the data is tested so that in case of disaster if you need to switch over to other service provider data will be available and can be restored as per your Recovery Time Objective (RTO).
4️⃣ Centralized Monitoring, Management, and Orchestration — Getting the single dashboard view of security posture is important. The security logs from all environments should be collected and processed at a single location so that uniform process will be applied to analyze and assign priorities to incidents. This will improve the efficiency of the sacred security professionals. The security tools and technologies deployed in a respective environment should be able to manage from the centralized management console this will help to manage the uniform rules and tool-specific policies across the environments.
All elements of security including tools, technologies, policies, configurations should be administered and managed centrally. This will make sure though the different CSPs may have different vendors still, you will be able to have consistent security policies and security posture.
5️⃣ Identity and Access Management –Security architect should not create separate identity silos for providing the cloud deployments. Each cloud deployment may have unique accounts within each of those providers and applications. To resolve this issue organizations should look for a centralized Identity and Access Management (IDAM) service that has capability manage all users’ access and authentication before they get access to any applications in the multi-cloud environment. This may include using your organizational directory for employees and utilizing federated identity solution (SAML based) for customers, other third-party users like partners. This will help an organization to easily and securely access the data and applications deployed in multiple CSP via single sign-on.
Multi-cloud Security Framework
The following picture depicts the high-level Multi-Cloud Cyber-security framework. This depicts the secure connectivity between the clouds, end users — may it be employees or third-party users from wherever they are assessing the applications, either form the enterprise environment or from anywhere. This can be accomplished by availing for Network as a Service (NaaS).
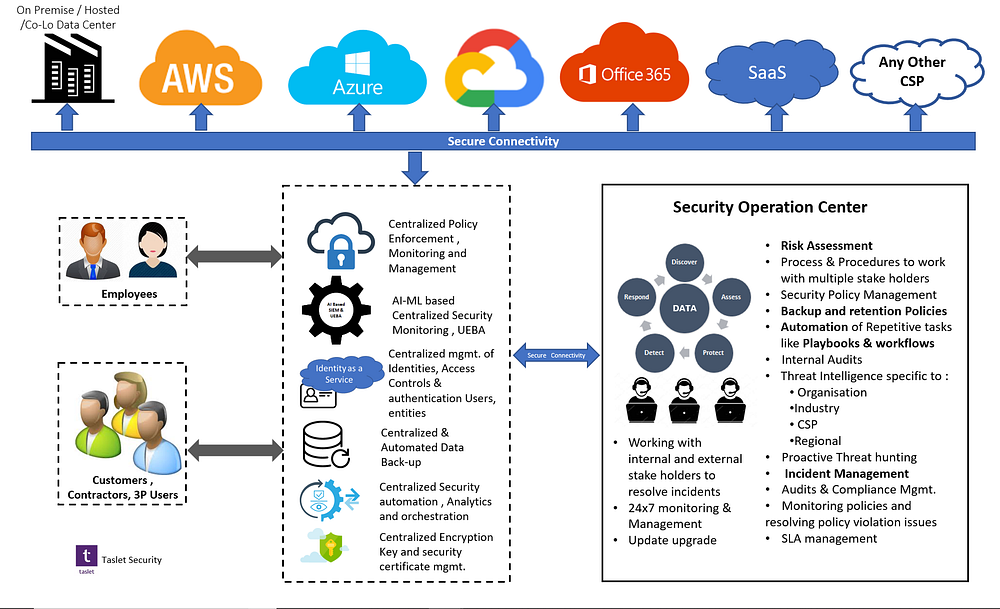
Irrespective of where the workload/application is deployed, security policies will be maintained as per the policy definitions and this can be achieved by utilizing the CASB or other centralized policy management solution which can span across the multiple clouds and data centers/hosted facilities. This solution should have the capability to enforce, monitor and manage the policies uniformly.
Logs from the different CSP environment involved in providing services should be gathered at a central location for centralized security monitoring, event analysis, and incident management. This will give the single view of the emerging threats across the organizations data assets. This Artificial Intelligence (AI) / Machine Learning (ML) based solution with capability of User and Entity Behavior Analysis (UEBA) will help to reduce the efforts and anomaly detection time which in turn will reduce the incident contentment time and cost of data breach.
All the users who want to access the application will be going through the centralized identity access management solution either as IDaaS as a service or the IDAM solution that is capable of accommodating the federated identity and managing different types of users, provide single sign-on and integrate or have the multi-factor authentication feature.
Having a centralized data backup solution will make sure that data from all the different environment will be available when it is most needed during the disaster.
The centralized automation, analytics and monitoring solution that needs to be utilized for managing the security infrastructure across the different environment. This can be the tool used for IT infra orchestration which can encompass to the security tools and technologies.
The encryption keys and the certificates should be managed from the central key vault or HSM solution.
Last but not the list, the Security Operation Center (SOC) should be empowered with the automation tools that help to automate playbooks and workflows e.g. getting the workflow automated for change request approval.
To Sum It Up
I would like to summarize this article by quoting Vivek Kundra, former federal CIO of United States
“Cloud computing is often far more secure than traditional computing because companies like Google and Amazon can attract and retain cyber-security personnel of a higher quality than many governmental agencies.”
This is not only applicable to the government agencies but looking at the cyber-security skill set shortage it is applicable to most of the organizations.
Skills are one part of the security equation, we need to have tools to empower these skilled resources. The need of the time is to have security tools that are powered by Artificial Intelligence and Machine Learning (AI-ML), tools that can encompass across the cloud vendors, automate the repetitive processes and can execute remediation irrespective of which cloud service providers environment needs mitigation. Tools should also able to proactively detect anomalies across the cloud providers by performing user, entity and network analysis, correlate it to provide the risk score. This will help not only getting a centralized view of security risks and improve the security posture but also identify the security attacks at early stages of cyber kill chain to reduce time and cost of security incident management, faster recovery from the incidents.









